v1 Overview
For v1, Fairblock's blockchain, the fairyring chain uses Threhsold IBE (Condition ID Based Encryption) to allow users to encrypt transactions using a public key,
which then decrypts and executes automatically at the target height.
The following flow gives an idea of how fairyring v1 works.
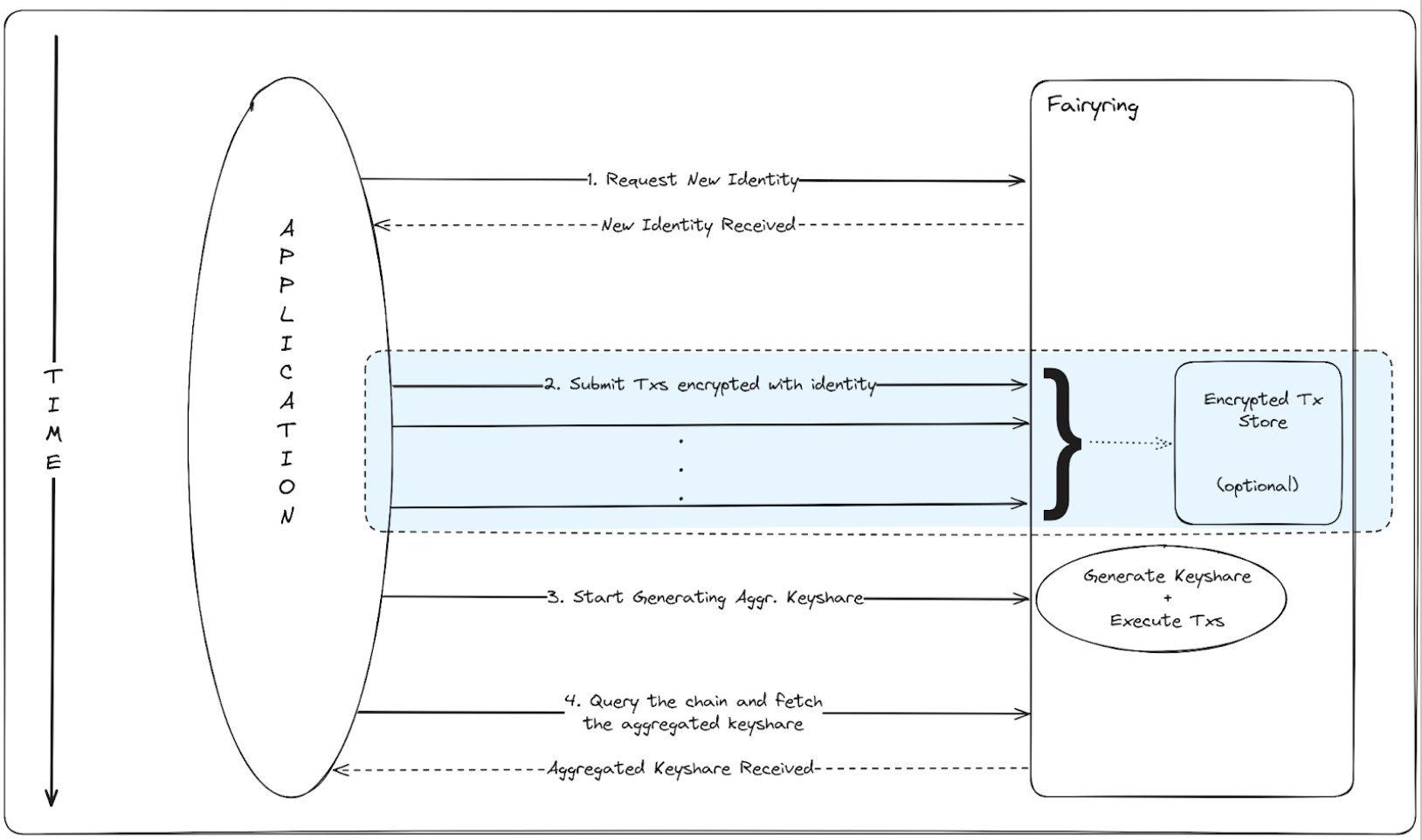
Apps refer to applications living on EVMs, and/or blockchains themselves, like those in the cosmos ecosystem.
Apps have active communication with the FairyRing chain. This communication mainly consists of the following steps:
- App listens to the FairyRing for new Master Public Keys (MPKs) to encrypt their respective transactions.
- FairyRing listens for a condition, and corresponding ID, to trigger generating a decryption key (keyshare).
- Once generated, keyshare is shared with the respective App. The App then executes the transaction at the beginning of the block to avoid risks arising from delayed execution.
Apps can do this because their EVMs will have access to a immutable contract exposing necessary function for encryption, decryption and execution, due to a Fairblock precompile being integrated into said EVM. Blockchains that also serve as applications themselves, like in the cosmos ecosystem, add on the x/pep module to communicate with the fairyring chain, which is elaborated further in this section.
In addition to communicating and unlocking encryption and conditional decryption/execution for destination chains, the
fairyringchain can have its own thriving ecosystem as other blockchains do. This is possible because any encrypted transactions can also automatically be decrypted and executed on thefairyringwhen a decryption key is made available.
The later pages in this section covers the detailed fundamentals of Fairblock. These include:
The Cryptography
The Network
- The purpose of Master Public Keys (MPKs), and how they are used to encrypt transactions.
- How MPKs and Decryption Keys (keyshares) are generated using the
fairyringand its validators in a decentralized manner. - How the keyshares are used to decrypt and enact automatic execution of an encrypted transaction at the beginning of a block.